Sep 10, 2012 at 11:33am ET by Adam Riff
There is little doubt that mobile search is the hot topic in the SEO world at the moment. Some brands are now finding that more than 30 percent of all searches come from mobile devices, according to Mobile Marketer. It’s fair to say that mobile search is quickly moving out of the Stone Age and into the digital age.
That’s the premise of a new insight paper, Mobile SEO Best Practices, published recently by my company, MediaWhiz (disclosure: I lead MediaWhiz’s search marketing and digital strategy divisions). In addition to a list of our top-10 tips for effective mobile SEO, the paper offers marketers a step-by-step guide to delivering effective mobile search campaigns.
The tips range from the simple (e.g., understanding the differences in how people search on mobile devices compared to their searches on desktops) to the complex, such as best practices to ensure a site’s mobile content can be properly viewed and crawled by search engines.
Below are my top-10 tips for effective mobile SEO. What are yours? Share your tips in the comments section.
1. Be A Search Psychologist
Searchers using mobile devices enter keyword queries differently than they do with desktop applications. They use shorter tail phrases.

Often, their searches are more local in nature and more prone to rely on Google’s Autocomplete feature complete a query. When optimizing meta title and descriptions, it is important to optimize for these shorter tail queries.

2. Think Social-first, Mobile-second
Mobile users tend to want to be “entertained,” and in many instances, they are connected 24/7 to their social media networks via apps. Content displayed for mobile users should be “entertaining.” When developing online content, think social-first, mobile-second.
Mobile sites should have social media links embedded on every page, as many smartphone users are connected to their social networks 24/7. Doing so will increase exposure, traffic and engagement by ensuring content is easily shared across social networks.
The examples below from Macy’s and Tiffany’s show how a social-first, mobile-second mindset with site design leads to more visually appealing mobile sites.


3. Know Where Mobile Searches Are Going
When optimizing webpages for mobile, ensure that the user agent for both searchers and for the search engine bots are going to the same version of the webpage. Don’t inadvertently get a site flagged for cloaking.
4. Size Matters
Mobile devices typically have touchscreens, and pressing a navigation link can be cumbersome. It’s important to streamline the navigation so users focus on the most important and/or most popular pages of a site.
Web developers should consider vertical menus. These are typically easier for users to maneuver when deciding which link to click on. In the example below, the Toys “R” Us mobile site utilizes vertical menus to optimal effect.

5. Develop To Scale; Don’t Scale To Fit
A successful mobile strategy includes developing a revamped site specific for mobile search. It should not merely be a scaled-down version of the desktop website, retrofitted for a smaller screen. Preferably webservers should be configured so that the mobile version of the site resides on a sub-domain leading with the “m.yourdomain.com.”
Many of the highest trafficked websites, and those that set the standards for best practices concerning user experience, have fully developed mobile versions of their websites to ensure mobile users get the best experience possible.
A good example of this is Twitter’s mobile site:

6. Link Location Matters
Each mobile-friendly page should have a link to the main desktop site — clearly marked — so access to the full site is not limited.
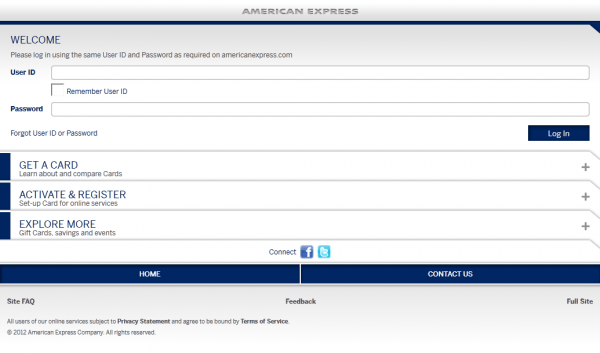
Example #1: The American Express website detects a mobile user agent and displays the mobile version of its site for best user experience. However, there is a link located at the bottom-right corner of the mobile site that allows users to change the user agent to the desktop version of the site.
Example #2: Subway has a link to “view full site” so users can easily and quickly switch to the version of the site that best fits their needs and device.

7. Don’t Forget The Click-to-Call
Make it easy for customers to call you directly from your mobile site. Each mobile-friendly page should have the phone number predominately displayed with easy click-to-call access embedded in every page, as seen in the GoDaddy.com mobile site below.

8. Use Rich Content Sparingly
Webpages with rich content (images and videos) are difficult to load on mobile operating systems. Reducing file sizes of rich content ensures those pages render properly on users’ mobile devices and give this highly sharable content better visibility.
A company whose mobile site effectively displays rich content without requiring long loading times is Coca-Cola:

9. Apps vs. Mobile-Friendly: Intent Matters
When deciding on application development versus mobile-friendly webpages, remember the intent of someone visiting a website versus using an application.
Applications are for resources that a person will use multiple times. The intent is that an application is either a resource or a business tool (e.g., mobile banking apps versus visiting a bank’s mobile website to learn more about home mortgage loan services).
For companies like Bank of America, which operate almost entirely on a transactional basis with their customers, a mobile app makes sense. For many companies, an app simply won’t be relevant or effective for their customers or business needs.

10. Embrace Search Engine Crawlers
Search engines understand that the mobile-friendly versions of your webpages are just that and not duplicitous content that could penalize your brand’s search rankings. Make sure search engines’ mobile content crawlers are directed (via setting the user agent) to the same mobile version that users are sent to. Doing so avoids content and penalties, such as cloaking.
Bonus Tip
Remember the primary reason consumers use mobile devices. Studies show that approximately 85 percent of people use mobile devices to “pass time,” “be amused” or for “entertainment reasons.” Develop mobile versions of your website with these aspects in mind for full engagement value.
Special thanks to Heather Fernandez, senior SEO strategist at MediaWhiz, who also contributed to this article. As a reminder, you can download a copy of MediaWhiz’s insight paper mentioned above “Mobile SEO Best Practices”, here.
Opinions expressed in the article are those of the guest author and not necessarily Search Engine Land.











